XSS in EasyVista Service Manager's new equipment Note field
Overview
A stored cross-site scripting (XSS) is available when registering a new equipment on EasyVista Service Manager 2018.1.181.1, on the Note field, allowing arbitrary javascript code to be executed on any user that visits the details page of the registered equipment. A filter is in place that attempts to prevent this, but it is incomplete, which makes it bypassable.
Details
After logging into the platform, a user is able to, among other functions, consult its own equipment. There is also a function available that allows registration of new equipment:
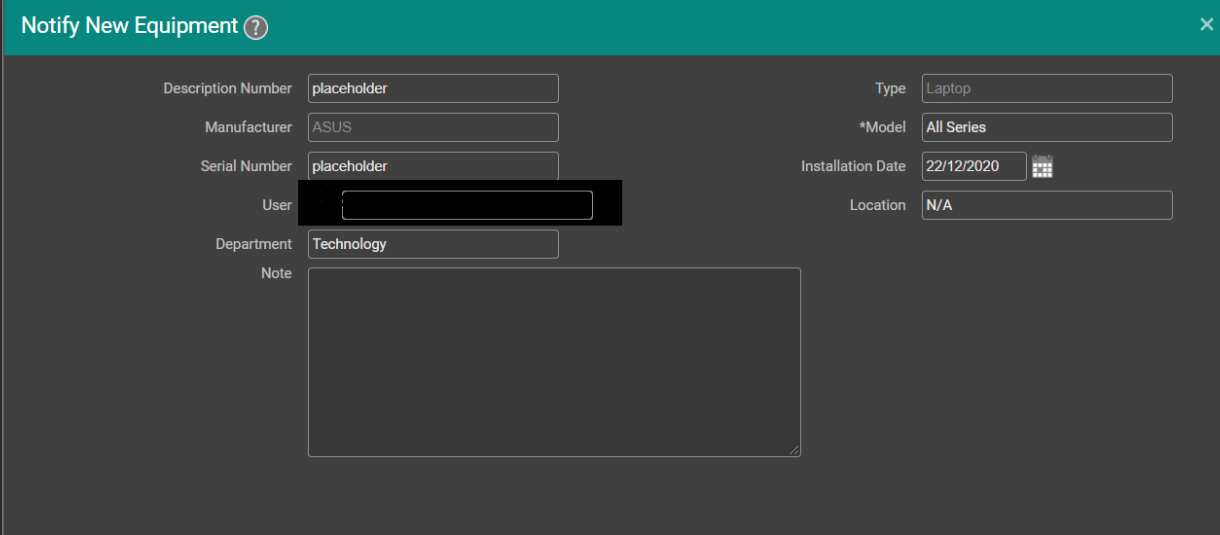
In the "Note" field there are protections in-place that correctly disallow (through filtering) the usage of javascript tags such as <script>.
However, it is possible to bypass it and inject valid javascript code by using different syntaxes that do not use the <script> tag.
The payload tested, shown below, was <img src=x onerror="alert('xss')"/>
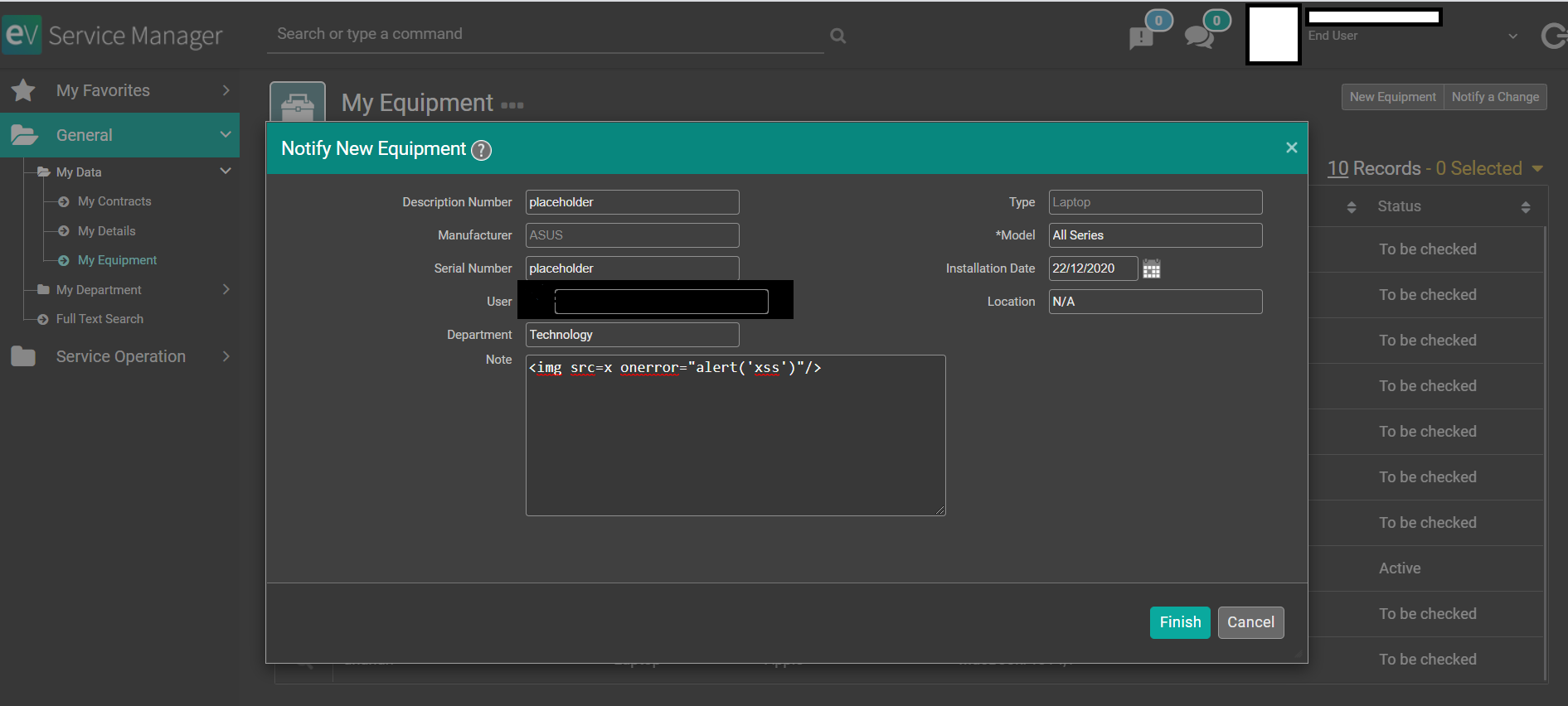
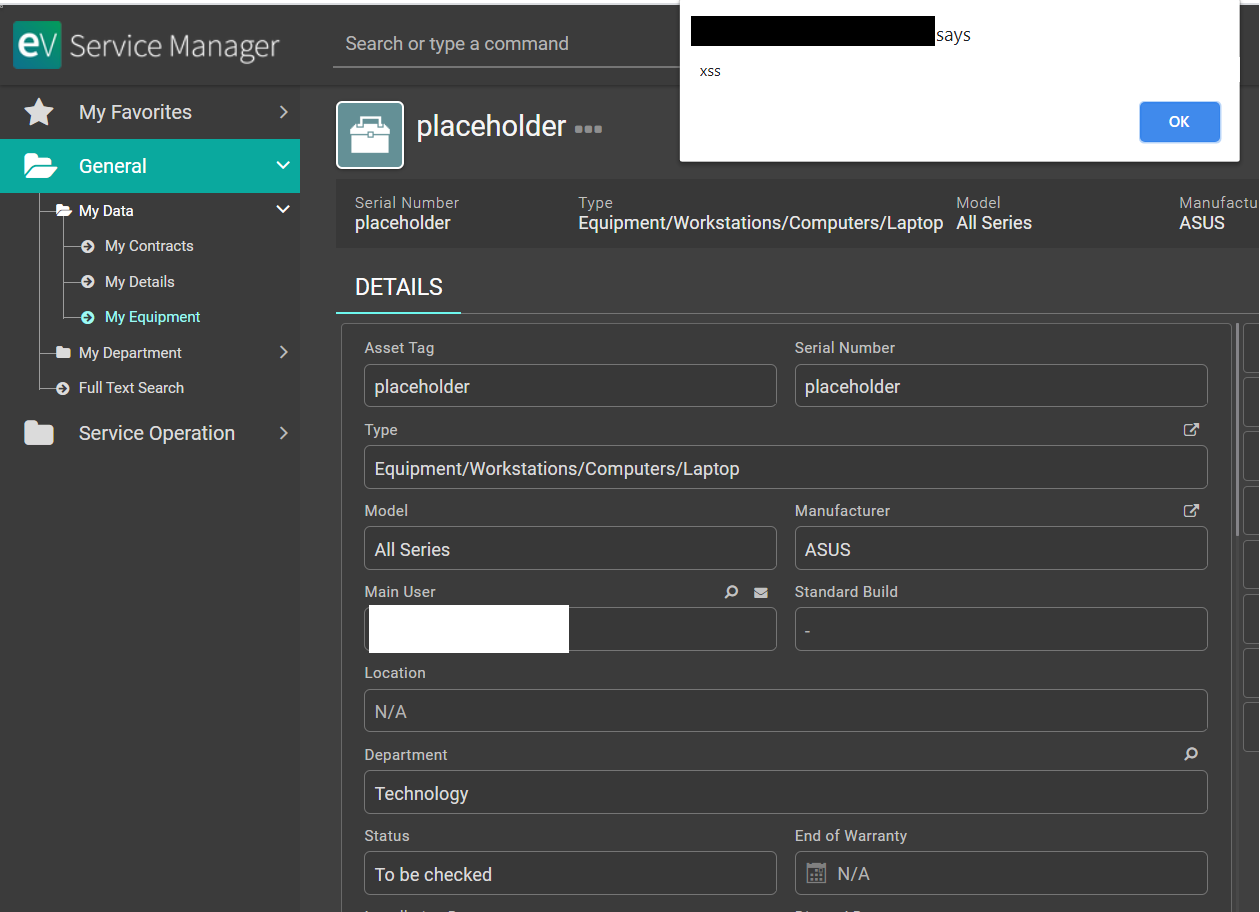
After submitting this new equipment entry, we incur into a case of stored cross-site scripting (XSS) where any other user - including administrators - that would consult the user's equipment would have arbitrary javascript code being executed in their own browser. Please refer to the proceeding image where the "alert('xss')" code that was input in the "Note" field popped up an alert on the victim's browser with the "xss" text in it. Notice that this javascript code can be replaced by more malicious code.
There is great variety of attacks based on XSS. These commonly include transmitting private data - such as cookies or other session information - to the attacker, redirecting the victim to web content controlled by the attacker, or performing other malicious operations on the user's machine under the guise of the vulnerable website.
Timeline
Dec 22 / 2020 - Reached out to EasyVista to identify the best process to report a security vulnerability.
Feb 11 / 2021 - After a second attempt, EasyVista suggested reaching out to their security e-mail address to report the issue.
Feb 11 / 2021 - Vulnerability was reported to EasyVista's Security team.
May 07 / 2021 - Contacted again EasyVista asking for updates.
May 07 / 2021 - EasyVista Senior executive confirmed that the issue was successfully reproduced and fixed on the latest EasyVista Service Manager version.
Final notes
I wish to relay all my best wishes to EasyVista's security team for its straightforward approach to the reported security issue and to the security senior executive for its cordial relaying of the actions that were taken.